Jakub Kroustek, a malware security researcher, was the first person to discover the .ETH ransomware. This is a completely new variant of the high-risk ransomware infection called Dharma. As soon as the infection has successfully infiltrated, it encrypts most of the stored files and it adds the “.ETH” extension to filenames as well as the developer’s email address and victim’s ID. So, it can rename the file’s name ‘sample.jpg’ to ‘smaple.jpg. id-1E857D00.[[email protected]].ETH.’
Hence, as soon as the data becomes encrypted, ETH generates a file which is then located on the desktop and opens a pop-up window. The text file and the pop-up window feature a similar message which states that the data in encrypted and that the person has to contact ETH’s developers if they want to restore it. Moreover, it states that a decryption code has to be bought if a person wants to restore the ETH.
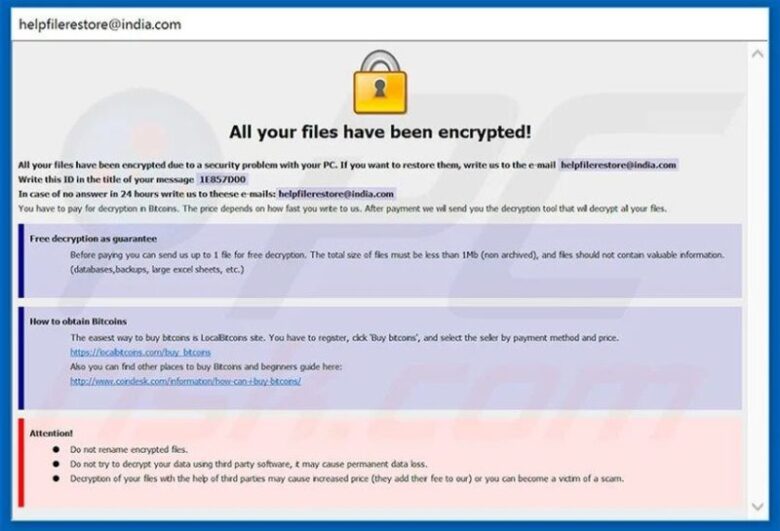
source:malwarewarrior.com
There is no known information what type of cryptography ETH uses, but the decryption requires a unique key generated individually for each victim. So, the victim is required to pay as the developers hide the keys and the price ranges between $500 and $1500 in Bitcoins or another cryptocurrency. However, you shouldn’t pay for it because it has been shown that cyber criminals will ignore you as soon as you pay. So, you should never contact such people and pay.
As there are no tools which can crack ETH and restore the data for free, but you can only restore everything from a backup. There are a number of ransomware-type viruses which are quite similar to ETH, including ITLOCK, LockerGoga, UNIT09, and Cyspt. These viruses differ mostly in the size of the ransom and the type of encryption algorithm. As most of them use cryptographies that generate unique decryption keys, you cannot obtain decryption without developers’ involvement.
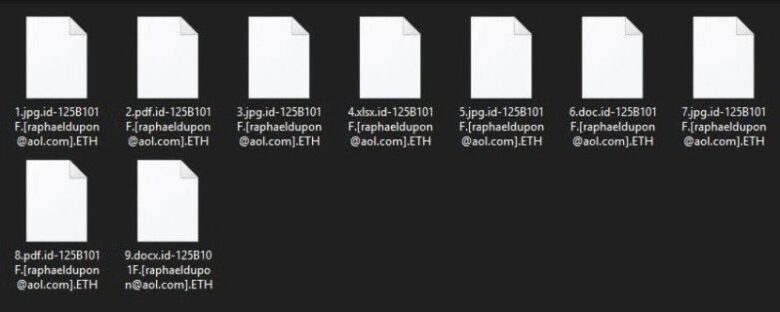
source:malwarewarrior.com
There are only two possible ways you can do the decryption, having certain bugs/flaws or if the ransomware isn’t completely developed. Thus, make sure you store your backup data on remote servers so they don’t get encrypted together with regular data.
How Does .ETH Infect the Computer?
The answer to this question seems to be a complete mystery, but it looks like cyber criminals mostly use software cracking tools, spam email campaigns, trojans, fake updates, and third-party download sources.
Ways to Protect Yourself from Ransomware Infections
Most people get computer infections due to carelessness and ignorance. So, the first thing to get yourself protected from ransomware infections is being cautious, always carefully analyze everything you receive and download, and have a legitimate anti-virus/anti-spyware suite installed and running.

source:cureyoursystem.com
However, if your computer gets infected with ETH, you should first run a scan with Spyhunter for Windows to automatically remove it. This removal process of the ETH virus can be quite complicated and time-consuming. Removal instructions can be found on the MySpyBot.com website.
Moreover, you can also remove the ETH virus using safe mode with networking or using a System Restore. You should also remember to always keep regular up-to-date backups which will help you lower the risk of damage from ransomware infections.

