With employees having access to a wide range of device both at the office and when working remotely, security can be quite challenging. As more companies started implementing Bring Your Own Device (BYOD) solutions, it is more important than ever that organization protect against unauthorized attacks and risky behavior.
One way to boost their data security is through a process that is called endpoint security management. In this article, you will be able to learn what it is, how does it work, as well as why it is important. Let’s take a look:
What is Endpoint Security Management?
Endpoint security management is a solution that requires endpoint devices to comply with a set of criteria before they gain access to any network resources. Endpoint devices include computers, laptops, tablets, and smartphones, as well as other, specialized equipment such as POS (point of sale) terminals.
How Does it Work?
These software solutions usually work by using a client/server model, in which a centrally managed server host a security software and a client program is installed on every network device that has to be monitored. New technologies allow the endpoint security program to be cloud-based with both security programs and host servers being monitored by a vendor.
According to the experts from Corptek Cybersecurity, whatever delivery method you chose to use, when a client device tries to access the network, the server ill try to validate the user’s identity by scanning the device in order to ensure that it complies with the necessary security policies prior to granting them access to the network.
Common features of Endpoint Security Management Software
Some usual features include:
- Insider threat protection
- Data loss protection
- Application whitelisting
- Email, disk, and endpoint encryption
- Data classification
- Network access control
- Privileged user control
The Importance of Endpoint Encryption and Application Control
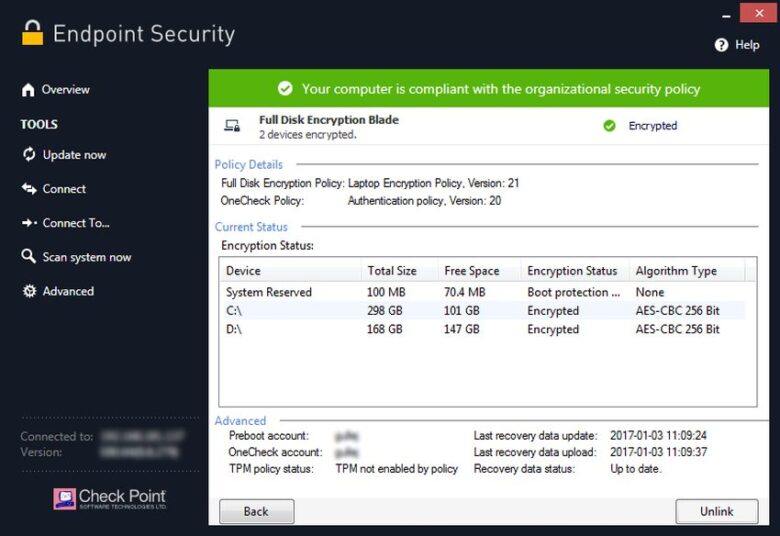
The two most important parts of this software include application control and encryption. The encryption allows the users to entirely encrypt company data on all devices including smartphones and laptop, and individuals folders, files, and removable media. Application control is what prevents unauthorized execution of the application.
This can help solve the issue of employees downloading a potentially dangerous or unauthorized application that could lead to major complications later on. As you already know and as already mentioned, employees are now relying on their mobile phones more than ever, hence, these remote work arrangement can effectively solve a company network security problem. Useful endpoint security is important to make sure that your employees are protected no matter where they are and on what device they access sensitive company data.
Conclusion
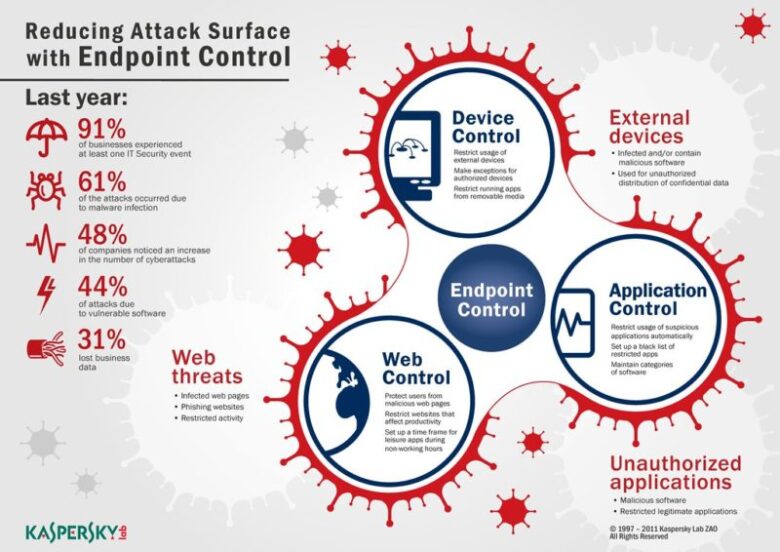
You should know by now that ant device can be a subject to an endpoint attack. And the objective of ant endpoint security management solution is to prevent and block unauthorized access through any devices that contain sensitive and important company data. Hence, if you did not implement endpoint security software in your company, do not waste any more time and start planning your security strategy.