What are Cyber Essentials Schemes?
You guessed it right, it is related to all that virtual stuff about which a layperson would not be interested in, but it is useful to businesses when it comes to its practicality. It is a government-produced business industry-supported scheme that helps ventures get protection against cyber-attack, which mainly involves virtual hacking and other malicious threats.
It usually helps out businesses figure their weak links in stored business accounts and credentials while also providing or preferring ideal basic controls to lessen the risk of cyber-attack.
These essentials have been of immense importance to the UK government; they made it a mandatory step towards carrying the ventures with them. As the government would not do business with a particular company unless it knows the companies you do business with are secured from cyber-attack.

Hence, certification of cyber essentials is of great significance as the government of the UK has made it essential as the name itself to protect personal business information, accounts and credentials. According to the CyberSmart, the reason behind this decision is so businesses could achieve trustworthiness through these documents confirming specific venture’s cyber security and protected certification for business trading/activities.
So does your Business need it?
Those that go through the cyber essential certification process clearly indicate to interested investors or other parties that it has an active role in society against recent threats existing or cyber-attack in this case as also representing the steps taken against malicious virtual threats to achieve data protection proving it be reliable.
The National Cyber Security Center of the UK states that going through at least one of the steps required for cyber essentials can protect a venture form 80% of computerized-attacks while appearing to interested parties as to privacy concerned. These perks can formulate into a much richer advantage because these perks can ensure competitive benefit as protection against computerized threats is a significant concern to suppliers.

Numbers show that only 14% of businesses try to opt for cyber essential schemes to mitigate their problems leading towards the inevitable of 60% of businesses going bankrupt because of computerized-attacks, which means survival is impossible without this process.
Hackers in this case usually aim at customers’ records, financial information, employee records, etc. Generally, to make it as disorientated as possible for businesses to run their day to day activities. These numbers communicate in most clear manner urging the importance of cyber essentials schemes which would eventually help companies to prevent these anticipated consequences.
More about it:
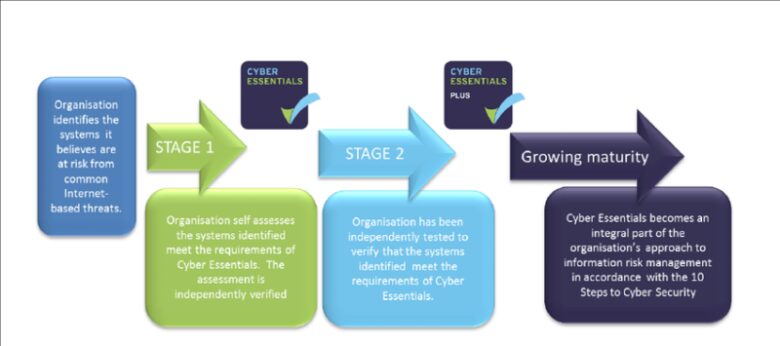
There are numerous ways to apply these schemes; the overview of these would be to go through a questionnaire often provided by virtual protection agencies. These schemes if used practically needs to be planned out efficiently starting from ‘Cyber Essentials certification’ under which leaves you with two types of choices;
- Cyber Essentials
- Cyber Essentials plus
Agencies offer both of these certifications, ‘a’ is awarded and verified through a detailed self-assessment while ‘b’ provides not only self-assessment but also a further external testing and on-site assessments ensuring security and prevention.
These certifications are not free either, charges vary, but in the UK, it ranges from £200-3000 and will be cumulative.
Measures for prevention:

As always, prevention is better than cure, so measures for the necessary level of security can be many and surprisingly affordable even for smaller businesses. Using strong passwords for business information could help, following on using foreign breach detectors to keep a strict eye for cyber threats. Similarly, putting up a gate between the internet and your system would prove to be quite helpful possible by firewalls.


